Security is a big deal for us. The data we put into our phones today is equivalent to the information people used to scrawl on tiny pieces of paper and stuff in their wardrobe in the old days. Having a phone that does not encrypt your valuable data is like leaving your house unlocked with a sign in the front saying, “Unlocked home, come get it!”
That’s why we’ve added full database encryption in DejaOffice. We don’t just encrypt select data types like notes. The entire DejaOffice database that resides on your phone is encrypted and locked. You can choose from a pattern-match challenge or an alpha-numeric challenge to unlock the database.

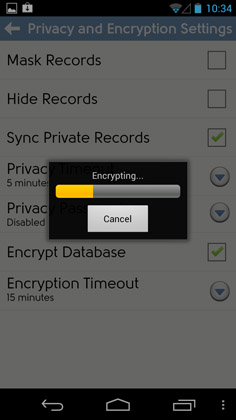

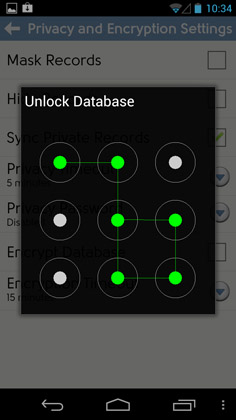
Download DejaOffice 2.2 free from www.dejaoffice.com/androidapp
By proactively managing your energy procurement strategy, you'll not only reduce costs but also contribute…
the modern workplace using remote work monitoring software must account for ethical leadership, employee input,…
Rather than handing easy wins to cybercriminals, organizational leaders should do what’s necessary to put…
When you buy followers from a trustworthy source, you’re not purchasing the kind of attention…
Building a YouTube Brand Channel is a change in mindset, not only a checkbox. Treat…
Integrating with the best trading platform tools and services, cloud solutions empower traders to analyze…