What Are DNS Records?
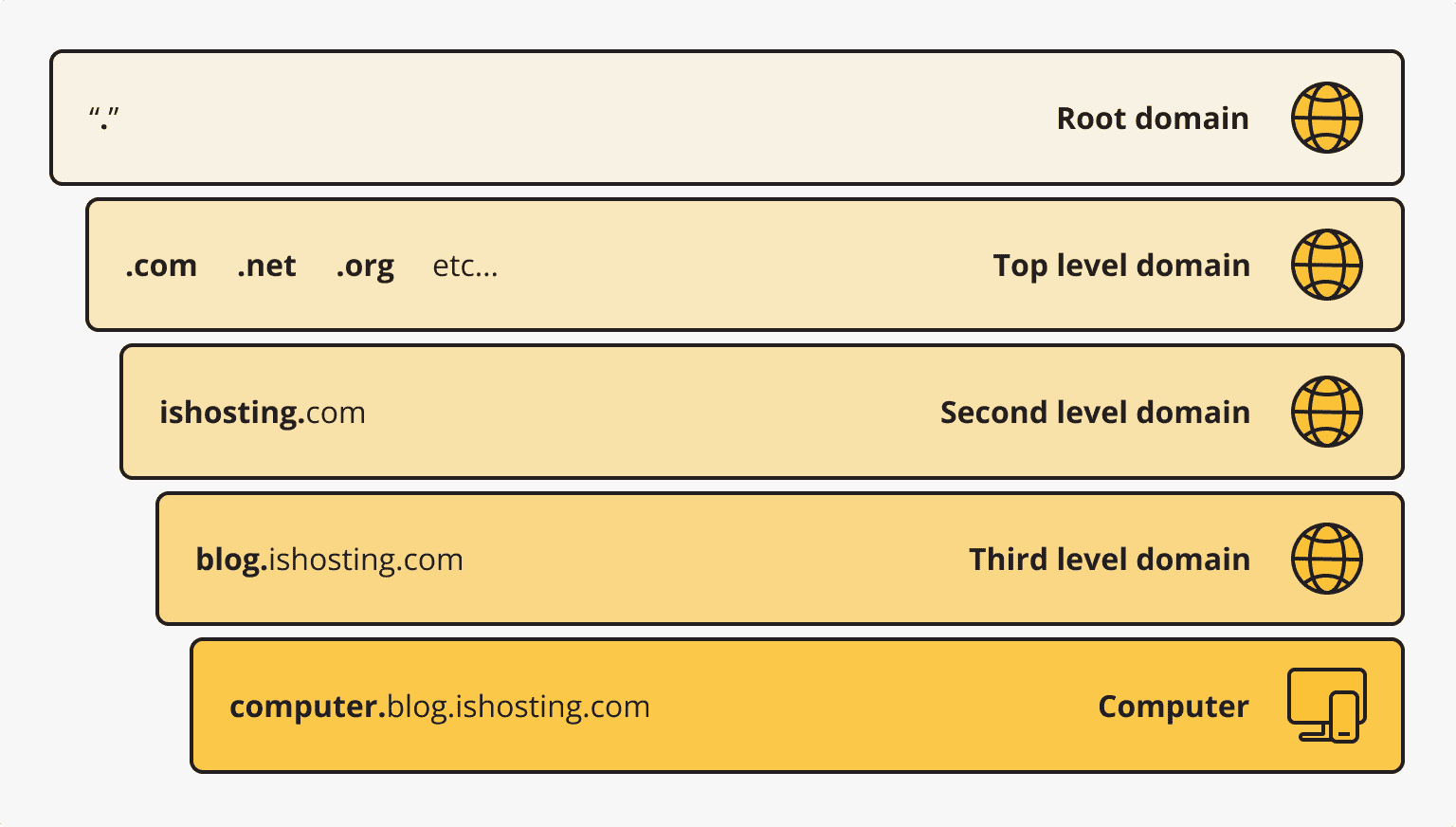
At the dawn of the formation and popularization of the internet, users searched for information by employing IP addresses. The first internet protocol (IP) standard appeared in 1981. Each such address includes a set of four numbers from 0 to 255. But online clients found it incredibly inconvenient to memorize so many numerics, so domain (website) names appeared in 1984. They were a set of simple words that were plainer to remember as well as employ.
Nowadays, PCs are still using IPs to find the necessary websites. But such addresses are transformed from domain names that ordinary clients apply. Browsers employ DNS entries for such transformations. This name is probably familiar to every active internet user because some browser errors are related to it. So, let’s learn more about DNS and its features.
What Is ‘DNS Records for Domain Names’?
Source: ishosting.com
This system operates like a smartphone. The latter has a list of phone numbers, and each contact has a certain name. So, users don’t have to call certain people by applying for corresponding phone numbers. Instead, smartphone owners look for a necessary contact by its name. And then, a gadget calls the needed phone number related to the chosen contact name.
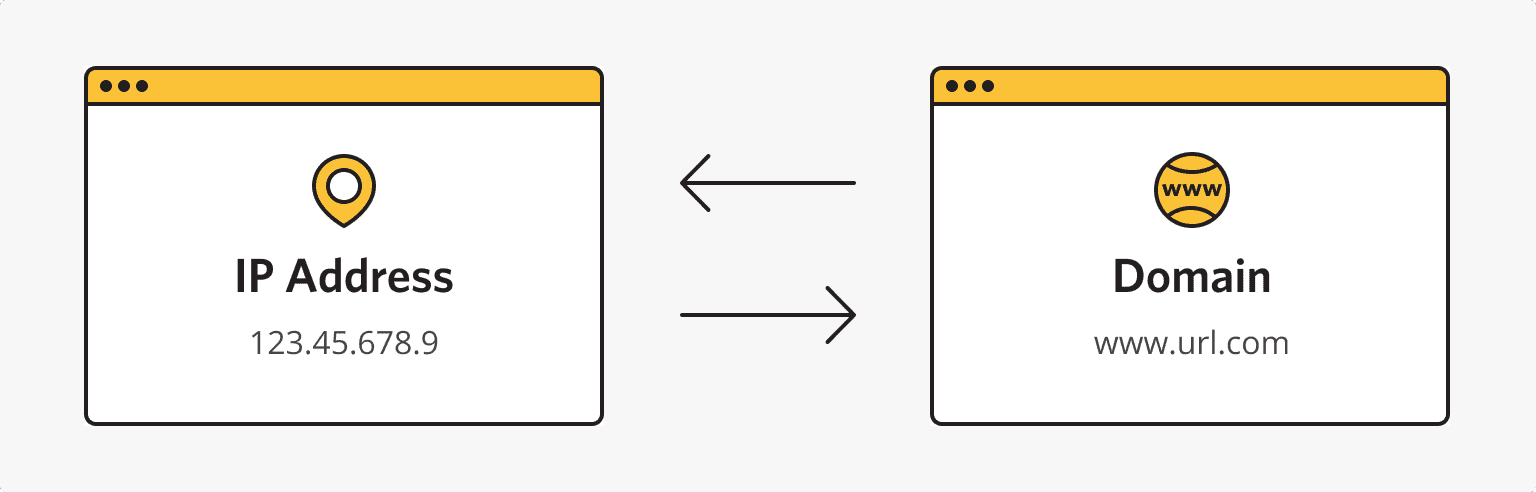
DNS entry meaning is almost the same. But here, clients enter a certain website name in a browser. Then the latter converts domains into IP addresses. DNS contains a database with IPs and their website names. So, the search goes through this data bank.
What Is a DNS Record Server?
Here, it’s necessary to look more closely at how the specified system works. So, it has the following operation algorithm:
- A user types the necessary website name in a browser address line. The web browser receives the entered query and sends it to a DNS server. Here, an appropriate domain and its IP address are searched.
- If a database on a server doesn’t contain the needed information, the request is sent to a higher-stage DNS.
- After the needed data is found, the browser receives a response, and the needed web page opens.
Source: ishosting.com
The reverse procedure is also possible here. Thus, users can find necessary domains by applying their IPs.
Where Are DNS Servers Placed?
The specified system is based on 13 main servers. However, developers made copies of these databases in various countries. Each server duplicate is assigned the same DNS server IP as the main one. Most such root data banks are placed in North America. But European countries, Australia, China, Brazil, Island, and some other developed states have numerous copies of these servers.
Types of DNS Servers
In most cases, such databases are proposed by internet providers. However, there are also own and paid DNS servers. The last ones stand out for their affordability as well as security. And own databases are commonly recommended to VPS holders. It’s free. Users should buy VPS on reputable platforms (like ishosting.com), though.
Why Don’t New Domains Start Working Immediately?
So, what is ‘DNS records’? These are pieces of data that are hosted on different-stage DNS servers, and such databases are regularly updated to add new website names. Internet providers use copies of root data banks. Such databases are named local servers, so first, browsers search for IPs in local servers. And these databases are commonly updated once every 24 hrs.
Therefore, local servers may not contain new domain names just after their creation. Consequently, browsers can’t find their IP addresses. Thus, users should wait up to 24 hours to visit a newly made website.
What Are DNS Zones?
The information above is true for domains that have the only IP. However, there are more complex situations. For example, subdomains, mail servers, etc., may be related to a particular website name. All such data is stored in specific files on DNS servers.
Specialists call the content of the said files DNS zone. What are the DNS records that the latter include? Here they are:
- A – this is the IP of a certain site related to an appropriate website name;
- MX – address of a mail server;
- CHAME – this record is usually applied for subdomain attachment;
- NS – that’s the address of a DNS database that stores resource records;
- TXT – this may include any text information about a domain;
- SPF – that’s a set of servers that are enabled to send emails on behalf of the specified website name;
- SOA – the original zone entry that includes the server details.
Consumers may see more information about DNS servers and website names, for instance, in the is*hosting blog.